Detecting Sensor-Based Repackaged Malware
Video
Team Information
Team Members
Shirish Singh, PhD Student, Department of Computer Science, Graduate School of Arts and Sciences, Columbia University
Faculty Advisor: Gail Kaiser, Professor of Computer Science; and Director of the Programming Systems Laboratory, Computer Science Department, Columbia University
Additional Authors
Xin Guo, Data Science Institute, Columbia University
Nancy Yun , Data Science Institute, Columbia University
Yukkie Liu, Data Science Institute, Columbia University
Jessie Ji, Data Science Institute, Columbia University
Huiyu Song, Data Science Institute, Columbia University
Abstract
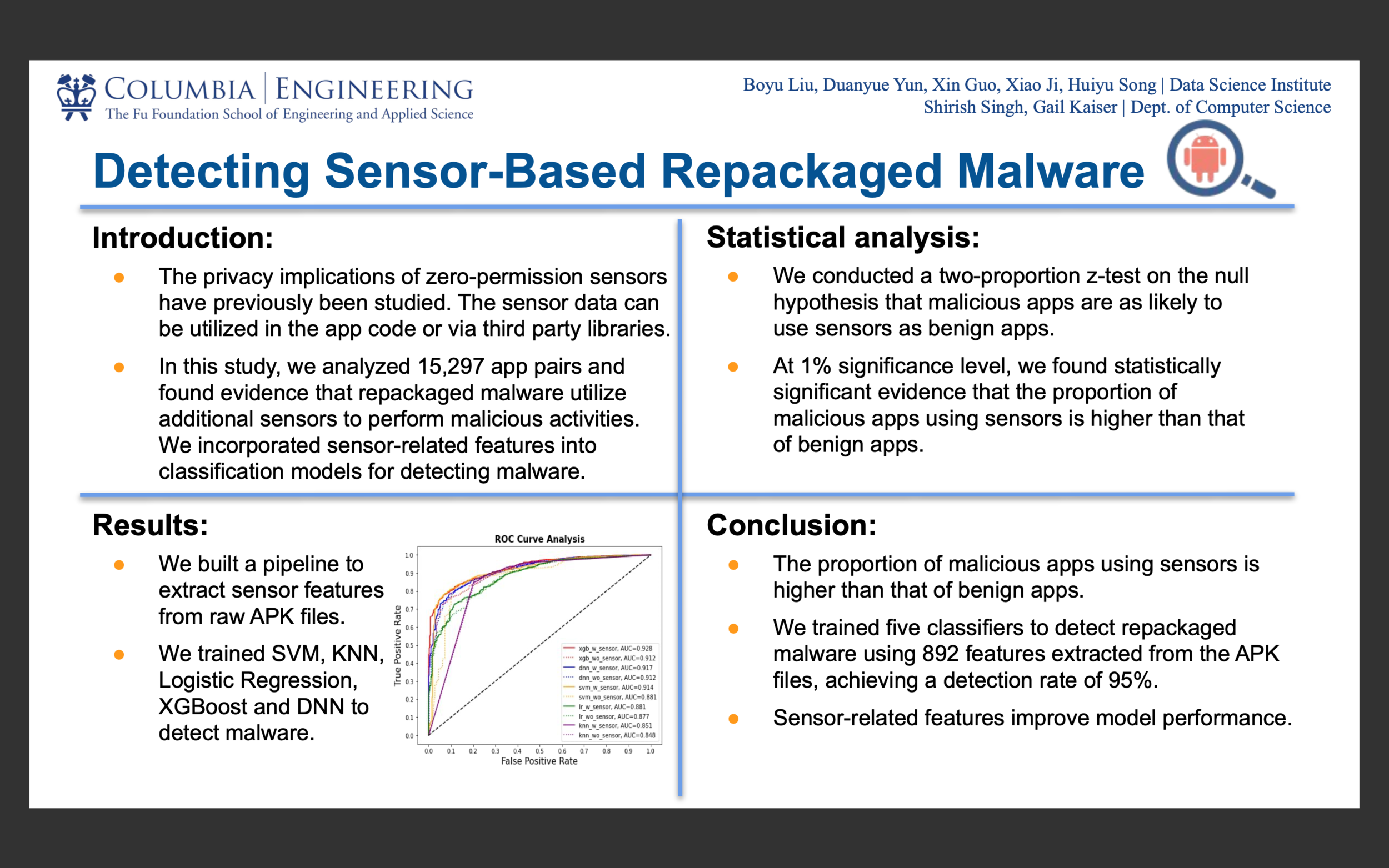
Android is the most targeted mobile OS. Studies have found that repackaging is one of the most common techniques that adversaries use to distribute malware, and detecting such malware can be difficult because they share large parts of the code with benign apps. Other studies have highlighted the privacy implications of zero-permission sensors. In this work, we investigate if repackaged malicious apps utilize more sensors than the benign counterpart for malicious purposes. We analyzed15,297 app pairs for sensor usage. We provide evidence that zero-permission sensors are indeed used by malicious apps to perform various activities. We use this information to train a robust classifier to detect repackaged malware.Contact this Team
Team Contact: Shirish Singh (use form to send email)